We security-adopted Microsoft Edge version 109 in January to allow 0patch users staying on Windows 7 or Windows Server 2008 R2 to browse the web securely. These Windows versions stopped getting security fixes for Edge, and Edge won't update beyond version 109 on them. Any PRO or Enterprise 0patch subscription now delivers critical security patches both for the operating system and the Edge browser, which makes for a lot of happy 0patch users.
There's one thing, though, that kept disturbing the peace: the pesky notification Edge was showing, reminding users that they should upgrade to Windows 10 or later, which they had clearly decided not to do. It makes sense for this warning to be displayed on a computer without 0patch, but with 0patch - nah, we needed to get it removed.
 |
| The persistent Edge notification, consuming screen real estate and narrowing user's world view |
Users asked, and we delivered. Our hot-patching technology allows us not only to fix security flaws but also to change functional behavior of Windows applications. Now that Edge has stabilized on version 109.0.1518.78, we created two patches that address said notification. Let's look at their effect.
FREE patch, delivered to all 0patch users regardless of their license or lack thereof
If you're using 0patch FREE, you're getting our 0day patches (as long as the vulnerability remains a 0day) but not all security patches. Users sometimes misunderstand what they're getting with 0patch FREE, and sometimes subscriptions expire without users noticing it, so we decided to use the Edge notification to warn them about it. With 0patch FREE, Edge will now show this message:
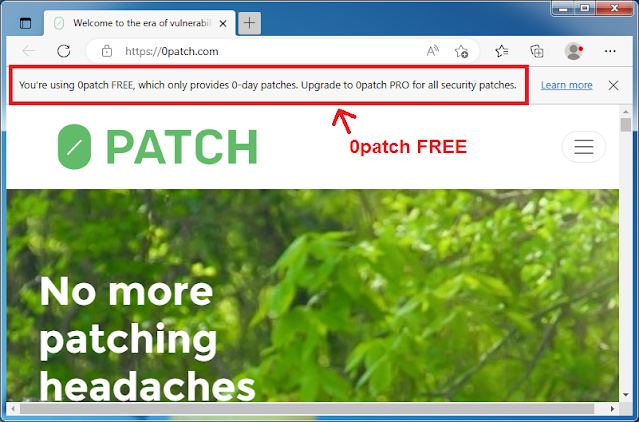 |
| 0patch FREE alerts you that you're not getting all security patches |
PRO patch, delivered to all 0patch users with PRO or Enterprise license
PRO and Enterprise 0patch users are getting all our security patches, so there's no need to take away their screen real estate or attention; Edge thus shows no notification on their computers:
 |
| No notification for PRO and Enterprise 0patch users |
In addition, Edge's About page shows that Edge is secured by 0patch:
 |
| It would take more code to remove the duplicate message and we prefer less code. |
Alternatively, one could also remove the Edge notification via registry, and our patches won't interfere: they'll still be getting applied, but even with 0patch FREE no notification will be shown.
If you're using 0patch and Edge on Windows 7 or Server 2008 R2, make sure to have Edge updated to the last available version (109.0.1518.78 *) and launch Edge to verify that it behaves as described above. If anything is unclear, contact our support by emailing support@0patch.com.
* Update 3/30/2023: Contrary to their announcement, Microsoft made a further Edge v109 update available to Windows 7 and Server 2008 R2 computers in March 2023, namely version 109.0.1518.95. We had to port our patches and recommend updating Edge to this version.